Digital Forensic And Investigation Capabilities
A question I often get asked relating to Digital Forensic and Investigation Capabilities is ‘what tools are required?’ – a question which is both easy, and difficult to answer. Easy, because the answer is ‘everything’ you need to ‘accomplish’ the task. Hard because, it is dependent on two factors which are as follows:
- The level of knowledge and skill which are in place
- The type and objective of engagements
It is important to keep in mind with every investigation, and the subsequent call on Digital Forensic Capabilities, that the most important element involved is robust, and defined process which will underpin all aspects of an engagement. Management of a Crime Scene, a robust Chain-of-Custody, process, with all the procedural underpinning of tagging, bagging, case management, and contemporaneous recording of events. In this capacity, it is why the level of knowledge and skill is so very important to establish. Fact is, within reason, anyone can use a Digital Forensic Tool to acquire, say a disk image, or a RAM dump – but only the accomplished professional applying robust processes and procedures can present such an artifact in a form which should sustain integrity under cross-examination. So, the first tool to place in the Digital Investigation/Forensic kit bag is that of a set of robust, and defined process.
At this juncture, I would also take time out to add into the kit bag a set of formalised standards which will assist the investigation during their engagements. Say the ISO/IEC 27035 in relation to Incident Management, the ISO/IEC 17025 in respect of calibration, and setting up a Forensic Laboratory.
The next question to satisfy is, what are the desired objectives of the organisation, or individual? If it is to satisfy an internal requirement to provision a First Responder (FR) Triage activity, with the intent to pass any deeper finding onto a contracted, external agency, then the required tools in the kit bag could be limited to say:
1. The underpin of processes and standards
2. Tools to record the scene-of-crime, including a digital camera, simple case management recording capabilities
3. Back-and-Tag processes to document, and record any First Response acquisitions
4. Secure Storage capabilities to maintain all case related materials under secure conditions with application of need-to-know, and need-to-access processes in place
With a – d in place and complemented with a quality toolset (screw driver etc), bags, tags etc, and the FR can accommodate the integrity of the case at the outset and is thus able to then handover as required to the second level of investigation and analysis which may be furnished by another internal department who are equipped to support the second-level processes, or a contracted outside agency, or in some cases even the Police who will supply the necessary specialist services to achieve the objective. So, the next important element to add into the mix is, ‘know the set limitations’.
OK, so we are agreeing now to enter into the deeper Investigation/Forensic engagement in which require a lower level of technological capabilities. So, before we start to buy in applications, let us agree on one thing. The applications we will be using will require some level of power to enable them to multitask, so for my own personal use I choice a Windows laptop accommodated with an i7 processor, a minimum of 8GB on board memory, a drive of at least 500GB, and an onboard TPM (Trusted Platform Module). Of course, you can go for a lower spec machine, but you will pay with wait-time whilst processing your case. I also find having a current license for VMWare can be a valuable addition to support engagements.
The next level of technological support I have is that of a high capacity, FIPS 140-2 Level 3, NCSC CPA (Foundation Level), Common Criteria drive to keep my cases materials secure and locked away in their own folder. This not only helps with case management, but also provisions support to prove that any acquired artifact, and other case-sensitive materials have been locked away from the potential of compromise, and corruption. My choice here comes in two forms, both supplied by iStorage. One is the diskAshur 2 which is available from 500GB, to 5TB, and the second is the more deskbound diskAshur DT offering 1 to 10TB of onboard storage.
As the technology demand grows, there are many must-have components and applications we need to add to the FR list – the first of which is a complete tool which will accommodate the acquisition, and analysis support of acquired artifacts and materials of evidential value, or materials discovered on computer systems, and/or their commonly associated mobile devices, and here my personal choice for use, and in support of specialist Digital Forensics Training I use the highly capable, and above all cost effective Belkasoft Evidence Center (BEC) which support capabilities to extract and carve deleted files, memory dumps, cloud deployments, iOS, Blackberry, Android, UFED (Universal Forensic Extraction Device) , JTAG and chip-off dumps, through to providing a mapping between entities (people) and objects (accounts) of investigative interest – this along with a very nice reporting feature make this an ideal partner to have alongside when engaging with a case, or students in the lecture environment.
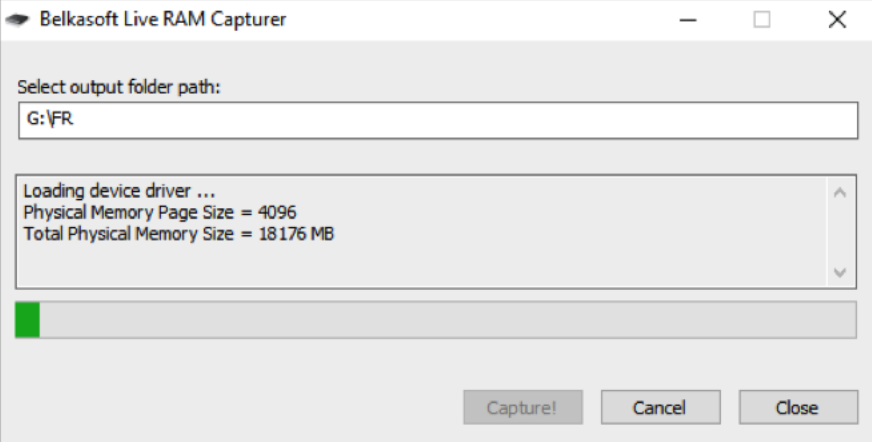
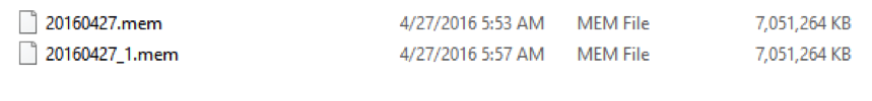
When it comes to acquiring the potential smoking gun which may exist within the dynamic RAM of a live system, Belkasoft also provide a free tool to acquire the ‘active’ and logical footprint – See Image 1 and 2 below (Note the path is G:\FR writing them directly to an attached iStorage Secure Drive for safe keeping).
1 – the RAM Capture in Progress
2 – Example of Captured. mem acquisitions
We must also provision a capability to ensure that we are considering the integrity of the object from which we are acquiring a copy from – say in the case of the hard drive denying the Windows Operating System the reach out with its 0x13 command to communicate with the object drive we are extracting a copy from. Here the Tableau Write Blocker range are a high recommendation to ensure we do not corrupt, damage or contaminate our Best Evidence.
There is also a plethora of other tools, and applications one may need to call for support from during a case, which can range from self-written bespoke quick-and-dirty code, WiFi sniffing capabilities to reverse engineer the potential path of abuse of compromise, through to sniffing tools like Wireshark, or other such utilities which allow the profile of DNS and routing to be subjected to examination.
OSINT (Open Source Intelligence) is yet another high value capability which can support the Investigator to be proactive with the acquisition of data which exists in the form of Social Media Comments, EPOCH Time Stamps, or possibly in the form of Metadata (data about data). To accommodate the aspect of Social Networking, this can be achieved within the Belkasoft Evidence Center which will graphically provide a representation of associations. Another very powerful tool used by professionals, government agencies, and police forces is Echosec which provides Geospatial, Mapping Services, News, Search Engine, Social Media Management, and the ability to home in on, and footprint a person, organisation, or object of interest.
In the space of OSINT there is a multitude of free tools, ranging from TweetDeck which provide real-time updates on Social Media interaction, through to Sentiment viz which allow a low level of tracking in real-time – See Image 3.
3 – Social Media Tracking
Above all, never forget when dealing with a Digital Investigation that the physical attributes live in the real world, and in some cases, the biological trace existing on the keyboard may just be that key piece of evidence that is required to prove a case, or to support a defense. So surgical gloves along with other secure handing processes are key skills need to be factored in.
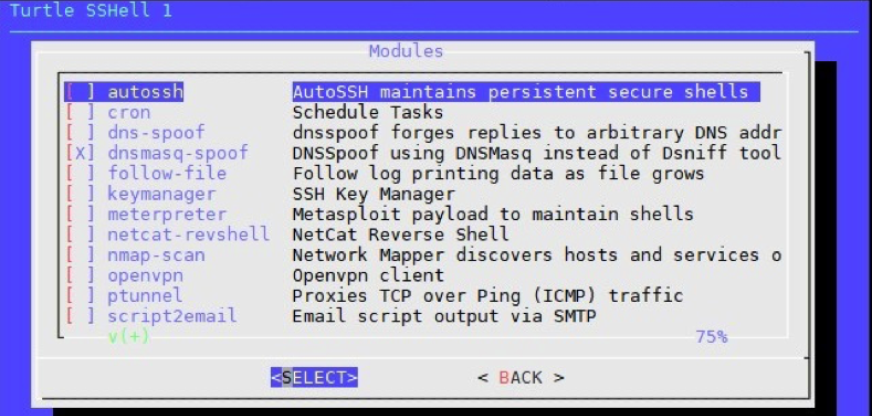
Of course, there are occasions when a Digital Forensics Investigation may need to move to the more proactive engagement, calling on the methodologies and application out of the world of Penetration Testing to acquire snippets of intelligence – all of course commensurate with the tone of regional legality and the subject laws. On such occasions as these it may be the services of more aggressive tools are required such as the Lan Turtle (see Image below for the Lan Turtle interface over ssh) from Hak5, their Rubber Ducky, or even the WiFi Pineapple. But again, I do emphasize that such aggressive engagements must be fully supported by a valid objective, be signed off by the client in question, and must satisfy the requirement that they are not, in any shape of form transgressing any local or international laws or legislations.
4 – LAN Turtle
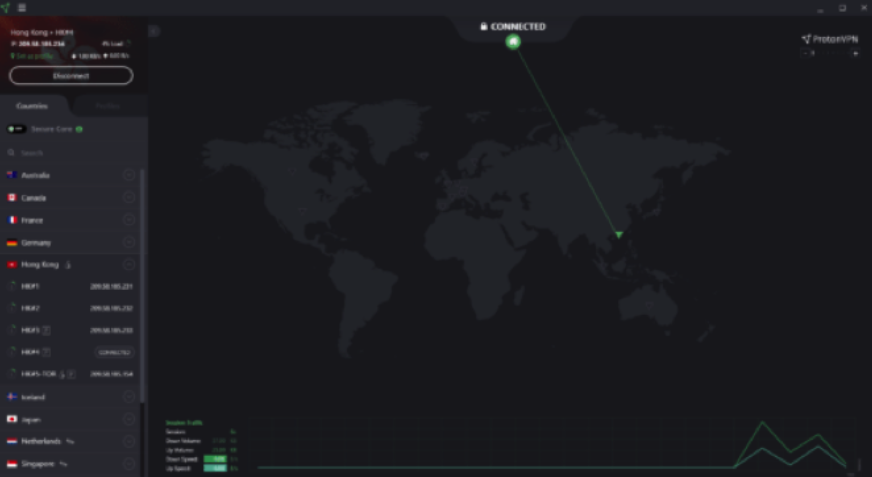
There will be occasions in which one must take steps to hide their own real logical footprint. Here the objective may be met using one of many VPN applications which give the user the ability to break out at any location they wish to – in my case, I favour the more trustworthy ProtonVPN, which being Swiss based does not fall under the potential gaze of the US Patriot Act. See Fig 5 which shows the connection routed via Hong Kong via an Onion Gateway:
5 – ProtonVPN Routing
Last but by no means least is my favourite sidekick of all – Hunchly’. Hunchly is a Browser Plug-in which allows the investigator to isolate his/her web searches to a case and then save it under one file name. Thus, this allows the on-line sessions to be tracked and recorded to capture all such on-line activities, Hunchly also allows the investigative user to tag files, and to generate reports of their on-line activities and searches. In a nutshell, Hunchly is a tool which provides the desirability of contemporaneous recordings, helping to ensure that the investigator never forgets their footsteps in relation to any given case. And of course, on occasions in which the investigator is engaged with multiples cases, Hunchly ensures that they do not get mixed up in the same pot.
6 – Hunchly
The above is just a tip-toe into the water of what can at time be a very complex discipline. However, I hope I have managed to set the ball rolling and invoke some thinking processes for any professional who is considering moving over into this interesting and demanding world – good luck.
About the Author
Prof. John Walker FBCS CISM CRISC CITP ITPC FRSA
Professor Walker is the facilitator on PLUS Specialty Training’s two Cyber Security courses, Certified Cyber Security Specialist, and Digital Forensics and Cyber Investigations.
John is a leading expert in the field of Cyber-Security. With over 30 years of international experience, he is a World Class Info-Crime, Cyber Security Researcher who has worked within the Covert Worlds of CESG, GCHQ, ‘TK’ Sky Technology, with the Security Services. He has delivered over 90 Global Presentations, and has originated over 100 Papers, & Articles on Cyber-Security.
He is actively involved with supporting the countering of eCrime, eFraud, and on-line Child Abuse, an ENISA CEI Listed Expert and an Editorial Member of the Cyber Security Research Institute (CRSI).
John is a Fellow of the British Computer Society (BCS), Fellow of the Royal Society of the Arts (RSA), Board Advisor to the Digital Trust and Writer for SC Magazine UK. He was the Originator of DarkWeb Threat Intelligence, CSIRT, Attack Remediation and Cyber Training Service/Platform, Accreditation Assessor and Academic Practitioner and Accredited Advisor to the Chartered Society of Forensic Sciences in the area of Digital/Cyber Forensics.
John is also a practicing Expert Witness in the area of IT, and the originator, and author of a CPD/MSc Module covering Digital Forensics, and Investigations.
Professor John Walker is a Visiting Professor at the School of Computing and Informatics, Nottingham Trent University (NTU), Visiting Professor/Lecturer at the University of Slavonia, CEO of HEXFORENSICS LTD, and Independent Consultant in the arena of IT Security and Forensics, and Security Analytics.
Related Blogs

Achieving Cyber Resilience within Organizations
I do not for one moment feel that any professional would argue that we are not facing a time of digital instability in our interwoven words of business, social media, or when we utilize some form of online service....

The Importance of Current Knowledge and Awareness in Cyber Security
When delivering the Meirc Certified Cyber Security Specialist course under the PLUS Specialty Training division, it is essential that we provide our attending participants with the very latest information on the state of...

How to Strive for Continual Improvement within IT
Most large companies use ITIL as the process framework for their IT operations. ITIL was in fact created at the end of the 1980’s, so something like 30 years ago. Even version 3 was first released ten years ago wit...

Creating a Successful IT strategy
For many IT managers, creating a high-quality IT strategy is probably one of the most difficult things to get right. In my experience, many IT manages struggle from the outset primarily and simply because they (and...