Long Cast Phishing

Having encountered several friends and associates who have suffered, what seemed to be sustained Phishing Campaigns I decided to invest some time and bated-responses to set up a little research experiment to prove, or disprove a suspected theory – but for me, theories are only proven when they are put to the test, so I set the stage.
All of those who I had spoken to, all had two factors in common, one of which was each one of them in a very small window of time had received multiple Phishing, Vishing communications with a hooked bait topic, ranging from special offers, locked Paypal Accounts, Apple ID update, through to Amazon tracking emails and unexpected files shared through Dropbox – all of which were fake, and sent by spammers within a period of just 5 days. The second common area was, without exception, each of my samples had completed an online document, providing the attacker with multiple pieces of information – e.g. Telephone number, email address etc.!
Below are some examples of the spams which were received:
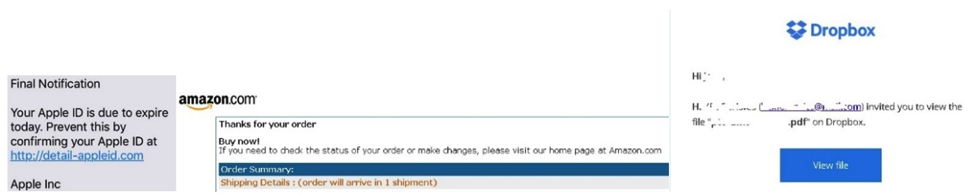
So to set the research ball rolling, I followed their actions on one of the danger-sites which seemed to have initiated a campaign – and as if by magic, the same conditions were replicated, and the phishing stared to pour into the email box, cell phones and by text – exactly the same condition that had been encountered by those who had shared their adverse experiences with me.
Conclusion
My conclusions here are somewhat obvious, born out of my first-hand encounter with what I call Long Cast Phishing:
- Where information is shared with a criminal entity (Hacker of otherwise) there is a high probability it will be subject to further abuse.
- Where multiple elements of information are exposed to a criminal entity. For example, email address, cell phone number etc. – expect each one of these elements to be potentially abused in their own channel of communication.
- When sensitive contact information is harvested by a criminal entity, such data assets have a value, so one may expect them to be shared on the Darkweb – Personal Information, or Credit Card information which has been supplied with the required details to transact a Card-Not Present opportunity is valuable and holds a resale value.
Putting the above considerations and conclusions into a real-world 2018 context, focuses the mind on the recent discoveries of security breaches the like of which has been observed at British Airways. The abuse of any valuable data assets will not necessarily be subject to immediate use – they may sit in the potential attackers’ hands until they are ready for exploitation to their own criminal advantage. However, one thing is for sure here, the dangers of encountering a Long Cast Phishing Campaign are common and active, and no matter the type of user, they must be served with security education and awareness to underpin their own personal cyber security.
If you would like to gain an in-depth understanding of cyber security and how to monitor IT operations to prevent cyber-attacks, learn about our Certified Cyber Security Specialist course here: https://www.meirc.com/training-courses/it-management/cyber-security-information-security-management-best-practice. As part of the course, you will also conduct a risk assessment of two different deployments based on the ISO27001 to identify any direct, or indirect threats, security exposures, or potential vulnerabilities.
About the Author
Prof. John Walker FBCS CISM CRISC CITP ITPC FRSA
John is a leading expert in the field of Cyber-Security. With over 30 years of international experience, he is a World Class Info-Crime, Cyber Security Researcher who has worked within the Covert Worlds of CESG, GCHQ, ‘TK’ Sky Technology, with the Security Services. He has delivered over 90 Global Presentations, and has originated over 100 Papers, & Articles on Cyber-Security.
He is actively involved with supporting the countering of eCrime, eFraud, and on-line Child Abuse, an ENISA CEI Listed Expert and an Editorial Member of the Cyber Security Research Institute (CRSI).
John is a Fellow of the British Computer Society (BCS), Fellow of the Royal Society of the Arts (RSA), Board Advisor to the Digital Trust and Writer for SC Magazine UK. He was the Originator of DarkWeb Threat Intelligence, CSIRT, Attack Remediation and Cyber Training Service/Platform, Accreditation Assessor and Academic Practitioner and Accredited Advisor to the Chartered Society of Forensic Sciences in the area of Digital/Cyber Forensics.
John is also a practicing Expert Witness in the area of IT, and the originator, and author of a CPD/MSc Module covering Digital Forensics, and Investigations. Professor John Walker is a Visiting Professor at the School of Computing and Informatics, Nottingham Trent University (NTU), Visiting Professor/Lecturer at the University of Slavonia, CEO of HEXFORENSICS LTD, and Independent Consultant in the arena of IT Security and Forensics, and Security Analytics.
Related Articles

Keeping It Safe: How to Protect the Systems That Run Our Lives
Imagine a world where you wake up one morning to find your air-conditioning…
Data Security in the Age of Ransomware
In the current era of cyber insecurity and the associated everyday dangers…

Value Creation with Artificial Intelligence
Our society creates petabytes of data, making predictions and improving…

What Can Pandemics Teach Us About Cyber Security?
We are living in a world in which we have either embraced technology,…